The NFC and contactless technology specialist has developed a way to turn NFC phones into “secured antennas” that can securely pull down sensitive data stored in the cloud and present it to a POS terminal or a contactless door lock — without the need to include an NFC secure element in the phone.

A cloud-based approach to managing sensitive data used to make secure NFC transactions holds a wide range of advantages over the use of a secure element within an NFC phone, Inside Secure‘s chief innovation officer Bruno Charrat has told NFC World, although the speed of current generation mobile data services mean it may be two to three years before the concept becomes a commercial reality.
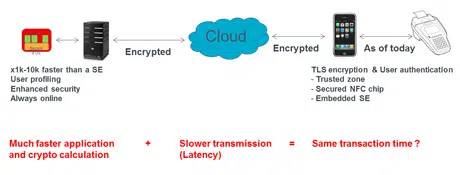
Cloud-based secure elements are a new concept that work on the principle that sensitive data is stored in the cloud rather than locally on the mobile phone. When the user conducts a transaction, the data is pulled from a remote virtual secure element in the cloud in encrypted format and “pulled through” the mobile phone to, say, a point-of-sale terminal. Last week, NFC World reported on US-based start-up SimplyTapp which has launched a payments service that works on a similar approach.
The approach has a number of fundamental advantages over current generation solutions, Charrat told NFC World:
- Today’s secure elements need to be large enough to store an unknown quantity of applications that the user may wish to add to their NFC phone as time goes by. They also need to provide high grade security to meet the requirements of organisations like EMVCo for storing card data. This makes the secure element expensive, says Charrat, and this cost could be eliminated or significantly reduced with a cloud-based approach. A much smaller and cheaper secure element could be used, which would only handle user and device authentication rather than storing data. Or a secure element could be avoided altogether by using a trusted zone within the phone’s main processor.
- It would be much simpler for secure service providers to implement NFC services, since there would be no need to integrate provisioning to a secure element on the phone itself.
- There would be no limit to the number of applications that an NFC phone could access, since these would live in the cloud on a secure server emulating a physical secure element.
- Consumers would be able to access all their applications from all their devices, since they would all be stored in one place on the cloud and could then be used on any of the individual’s NFC-enabled mobile phones, laptops or tablets.
- Since the system is fully online, fraud detection would be instant.
- NFC controller chips could be simpler and, therefore, both smaller and cheaper since they would not need to be able to handle the same range of functions.
- NFC phones would not need a dedicated mobile wallet in which information on services available is stored. Since the virtual secure element is stored in the cloud, users would be able to access and modify their mobile wallet services via a standard web browser. This would also reduce the need for secure service providers to develop different applications for different types of mobile phone, he added.
- The solution addresses an emerging issue of how to safely pass on an NFC phone to a new user or to send it safely in for repair without risking that sensitive data could be accessed by a third party, since card and other secret data would no longer be stored on the device itself.
- The solution would meet the requirements for ‘card present’ transactions since, like current generation secure element solutions, the NFC phone would appear to the POS device to be a standard chip card. There would also be no need for specific upgrades to hardware or software.
- A single NFC phone could be linked to multiple virtual secure elements, allowing any organisation to own its own secure element.
Key to gaining adoption, says Charrat, will be the ability to conduct transactions quickly enough and to provide very strong authentication of both the user and their mobile device.
The issue of speed will be addressed by putting a distributed computing architecture in place, something which Inside Secure has under development already available on the market, and by the increased availability of both in-store Wifi and 4G networks, says Charrat.
Because the secure element is now stored on a secure server, processing times are far quicker because much more computing power is available on the server than on the kind of secure element that can be included on a mobile phone. But network latency means that it can take a significant amount of time for a data request to reach the cloud servers and be returned to the POS device.
The ability to provide secure authentication of both the device user and the device itself will also be critical, says Charrat, and Inside Secure is also working on solutions to this issue.
“NFC today is so complex,” he told NFC World. “We need to change something. We are leveraging what the phone is capable of doing. Nothing will be local except the user authentication.”
Next: Visit the NFCW Expo to find new suppliers and solutions
Beside RSA and DES keys what’s so secure in EMV cards? POS terminals read all of the other data in clear text during normal NFC transaction anyways.
If keys are kept in the cloud ‘secure element’ why we then even need any secure NFC chip on the phone?
Why not just use QR code to encode the protected (encrypted and digitally signed card data) fetched from the cloud to the phone just before the transaction and let POS scan and decode that QR code?
Because the current unmodified POS can read/write virtual card by the NFC communication tunnel smootly, but if POS want to scan QR code from the phone screen, there are some hardware/software alteration is required.
Nothing new. At Chess IX we implemented secure cloud server technology for ticketing and payments already some years ago. It is in use to top-up the Mifare based NFC cards used in the Dutch Public Transport system and for NFC payments in Rabobank’s micro payment system Minitix using DESfire based NFC stickers. The same concept has been implemented using a Google Nexus smartphone. But without mass adaption of NFC smartphones there is not yet any commercial push to roll-out.