URI spoofing and redirection — where an authorised NFC tag is replaced with one that points to a resource under a fraudster’s control — is still an issue, says security researcher Collin Mulliner.
Fraunhofer Institute SIT researcher and trifinite group member Collin Mulliner has presented an update on his ground-breaking work in potential NFC vulnerabilites at 253C, the Chaos Computer Club‘s annual hacker convention.

Mulliner first reported on how NFC phones could be attacked in May 2008 in a presentation at EUSecWest. In that first research, using an early Nokia 6131 phone, Mulliner discovered that it was relatively easy to trick an NFC handset user into performing a harmful operation with their mobile phone without doing anything so complicated as attacking the NFC handset itself.
The potential weak link in the chain is the passive NFC tag, says Mulliner. It’s simplicity and low cost is its disadvantage as well as its advantage because it is easy and cheap for a fraudster (or just a trickster) to acquire the tags and to then replace an authorised tag with a fraudulent one of their own.
This means, for instance, that when an NFC handset owner interacts with a tag on a movie poster or tourist information map, instead of the tag performing the expected operation it would instead do whatever the fraudster had set it up to do.
Mulliner’s examples of how this could be exploited included:
- A tag set to send the browser on a user’s handset to a particular website could be replaced with one set to send the user to a different website.
- A smart poster could include a tag set to deliver a freephone number to a user’s handset. This could be replaced with a tag set to deliver a premium rate number belonging to the fraudster instead.
- A tag set to send a free SMS text containing the latest weather forecast could be replaced with one that instead placed an order for a premium ring tone.
Mulliner then took a look at how this all might work in the field, visiting Vienna and Frankfurt to look at both transit ticketing and vending machine applications.
In a group of four vending machines, for example, he identified that the NFC tags on machines B, C and D could be replaced with tags that point to vending machine A. Then, whenever anyone made a purchase at any of those machines, the item bought would be dispensed from machine A — straight into the waiting hands of the fraudster.
Mulliner also looked at the potential vulnerabiities of the existing SMS-based NFC ticketing system on Vienna’s Wiener Linien and OBB’s Handy-Ticket and also at RMV’s Handy Ticket system in Frankfurt.
Mulliner then presented his findings to Nokia who, he says, took them seriously and responded promptly.
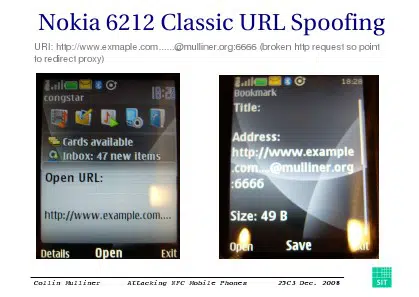
The result, he revealed at 253C, is that many of the issues uncovered during the initial testing have now been fixed — but there are still issues. “The Nokia 6212 Classic is not vulnerable to most of the bugs I found in the Nokia 6131 NFC,” Mulliner told the audience, “but URL spoofing is still possible.”
Mulliner presented his conclusions to the assembled hackers and security researchers at 25C3:
- Found some bugs in common NFC phone — Bugs are trivial but can be exploited
- NFC phones can be attacked in multiple ways — Phishing, malware, worms, denial-of-service
- Passive tags are the primary vector for attacks — Maybe make tags tamper proof? Use NFC point-to-point mode (active components on both sides; but these are more expensive)
- Users of early NFC services need to watch out! — Basically need to check content of tag every time
If you haven’t come across his work before, it’s worth taking the time to read through Collin Mulliner’s presentation slides (PDF) to gain a full understanding of the issues involved.
And if you’d like to then be reassured that there are ways of fixing the problems Mulliner has identified — albeit by adding a layer of significant complexity to the way things work — Dave Birch of Consult Hyperion has some good ideas on how this could be done.
Next: Visit the NFCW Expo to find new suppliers and solutions
These are not leaks of the NFC technology, the global way the data are exchanged with the web server is responsible in this particular case !